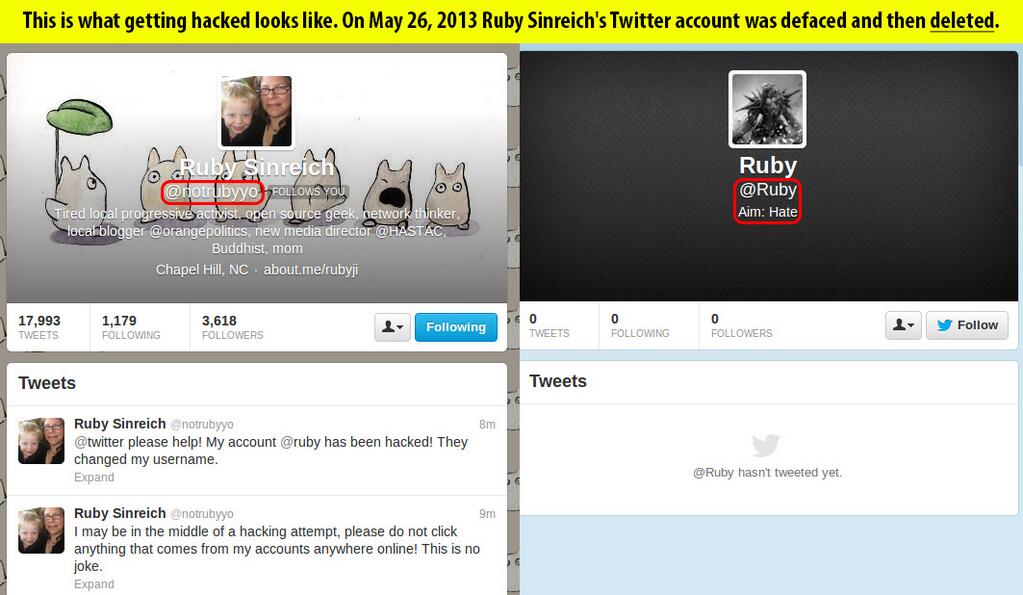
Cross-posted from MomsRising.org.
I don’t know about you, but the past year has been a real wake up call for me about the importance of digital security. I used to think of hackers as bored teenagers showing off for their friends, or scammers sending viruses and spam to people by the millions. But today’s online outlaws are much more sophisticated.
Not content to just blast misleading links at us, elite hackers have started spear phishing. This is a tactic that sends an e-mail to an individual with unique, personalized information making it look very real, and convincing the user to click through to a website where they will enter their login credentials. Some hackers also use social engineering (not technology) to trick people into giving away critical information that can then be leveraged to compromise accounts.
Unfortunately, we need to worry not only about obviously sensitive information like bank accounts and e-mails, even seemingly inconsequential accounts can be exploited to provide an opening. Once a hacker gets into any of your accounts, be it iTunes, Etsy, or Pinterest, they can use that information to access other services.
The threat to our privacy is real, and we have seen that there are people who may target us and access our data not just for commercial purposes but for political use. People and organizations that are working for social change have every reason to be concerned about how our personal information, organizational data, and private communications might be used.
Good security is a pain to implement, but every inconvenience for us is an even bigger hassle for a would-be hacker. Start now from wherever you are, and make incremental changes to improve your personal and organizational security.
OK, Ruby, we’re terrified! What do we do?
There is always room for improvement of our security practices, especially as we learn more about the threats that are out there. Here are my recommendations for where to start.
- Use randomized, unique passwords on every single site, and use a solid password manager like LastPass or 1Password to store them. Both have group options for setting up a whole team and sharing between them. Never send a password over e-mail or social media.
- Use multifactor (a.k.a. “two-step”) authentication for your e-mail, social media accounts, and any other service that offers it. Individual Gmail users can start here. If your organization uses Google services, you can require this for all users.
- Protect your website with HTTPS, especially if users are entering e-mail addresses and passwords. And use HTTPS Everywhere in your own browser to make your web traffic private.
- Secure your laptop and phone by setting them to require a password every time they start or wake up. Bonus: encrypt the data on them as well.
- Use a secure messaging app like Signal or WhatsApp for texting and calls on your phone.
- Don’t fall for phishing e-mails. If it smells bad, go directly to the source but don’t click any links in the message.
- Think about your threat model to identify unique risks to your organizations.
More resources
- Hackblossom created the very helpful DIY Guide to Feminist Cybersecurity that you never knew you needed.
- Me and My Shadow is a fantastic site with fun, educational information and even trainings you can download and use about online privacy.
- The Electronic Frontier Foundation has been advocating for Internet users’ rights for many years. Their Surveillance Self-Defense site includes a Security Starter Pack and covers a wide range of topics thoroughly.
- Find out if your accounts have been compromised with Have I Been Pwned.
- Crash Override exists to support people who are experiencing online abuse. Their Resource Center has links to many helpful guides and tools.
- A quick and dirty Surveillance Self-Defense Checklist from The Intercept.
- A longer read on Surveillance Self-Defense from the Trump Administration at The Intercept.
Here’s your reward for making it to the end of this challenging post! Freak out and laugh and get down all at the same time with Ashley Black learning about digital security with the help of Talib Kweli and others, on Full Frontal with Samantha Bee (NSFW).

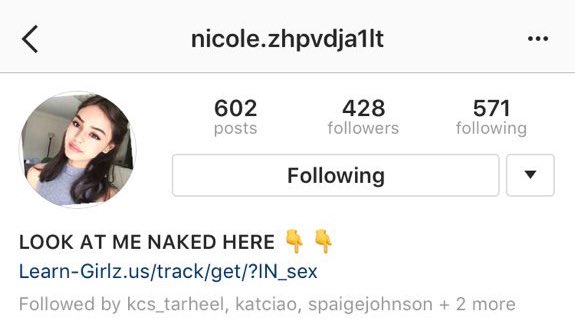
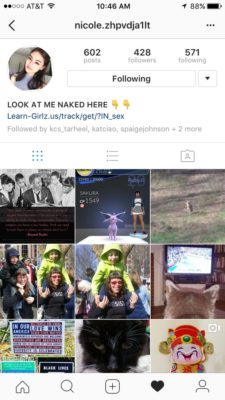 So
So